

Updated December 18, 2025
As a small business owner, cyber threats are a very real possibility. Instead of living in fear of data breaches, companies need to protect assets from threats online and vulnerabilities. Before moving toward these goals, businesses need cybersecurity budgets to guide their efforts and financial input.
Cybercrime is as big of a threat to small businesses as ever. An influx of remote work, additional endpoints, IoT, and SMB digital transformation has ushered in more security risks for companies without targeted cybersecurity measures.
The average cost of a single ransomware attack is $4.62 million. Don’t leave your IT security at the bottom of your priority list. Instead, invest in security solutions that will allow you peace of mind.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
While decision-makers likely understand the importance of security services, acknowledging and executing the need are two entirely different things. An early step in your execution plan should be building a budget and researching solutions in the market.
Creating a budget for cybersecurity services can be a challenge, especially for business owners who are new to the process. Companies can base their security and IT budget plans on our step-by-step guide.
The cost of cybersecurity services can vary significantly depending on the initiatives needed to protect the company from cyber risks effectively.
This means that the cost of cybersecurity services can range from a few hundred dollars to several thousand. The difference maker is that projects can range from an essential software and hardware solution to more comprehensive protection and managed services.
Determine how much your cybersecurity project will cost with our cybersecurity pricing guide.

What gets included in these budgets — big or small? These are the key components:
In-house employees are often your business's biggest vulnerabilities relative to cyber threats, especially since the pandemic. They have access to secure information that hackers seek and can sometimes be tricked by malware, ransomware attacks, or phishing schemes. Offering employee training opportunities increases your overall security and workers’ understanding of the ever-changing threat landscape.
Software and hardware solutions are the tools security teams will use to create your cybersecurity framework. These products can include firewalls, antivirus software, intrusion prevention systems, and more. The need for each of these services will vary based on the priorities your CIO or CISO determine for the project. It’s important to note that some of these costs will be one-off charges for purchase and installation while others will require recurring fees for maintenance and updates. Along with tools, cyber insurance can be bundled into this category.
Compliance and regulatory requirements ensure that your systems, policies, and employee training align with legal and industry-specific requirements. How much of your budget to allocate towards these compliance and regulatory requirements can depend on your business type and industry. Many industries, like healthcare, finance, and energy, are subject to strict regulations, including HIPAA, GDPR, and PCI DSS. Failing to meet industry standards can result in fines, reputational damage, and even loss of business licenses.
Allotting for compliance and regulatory requirements within your cybersecurity budget supports the audits, risk assessments, and documentation needed to create a structured, proactive protection plan and prove adherence to legal regulations and industry best practices. Ultimately, this can help you avoid costly legal penalties and maintain stakeholder trust.
There’s only one way to ensure that your security plan has a handle on the entire cybersecurity lifecycle: the proper implementation of each of these three components.
While there can be several costs associated with upkeeping cybersecurity systems, remember that investing in your security is key to protecting your business from breaches. Generally, it’s worth investing in best-in-class cyber solutions because they save you the devastating costs of dealing with a cyberattack and provide you with the peace of mind that your sensitive information is secure.
Not to mention, cybersecurity problems can have huge reputational impacts on your brand and the perceived quality of service you can provide. Don’t risk it — work with reputable cybersecurity professionals with a track record of delivering reliable protection.
Additional Reading: ‘5 Benefits of Cybersecurity Services for Small Businesses’
Building a cybersecurity budget requires decision-makers to consider a multitude of factors, both cost-related and quality-of-service related. Here are three simple steps that will give you a clear understanding of how to budget for cybersecurity services of your own:
Looking for a cybersecurity team to secure your assets? Connect with the best on Clutch.
Whether you’re a healthcare firm or a supply chain company, all organizations have vulnerabilities. The first step of planning your budget will be to determine security gaps in your current systems.
While this is easier said than done (you may need to hire a team for penetration testing or other security efforts), it is absolutely essential to grasp the current state of your cybersecurity systems.
Determining your budget allocations and areas of most need shouldn’t be anything close to guesswork. By spending time upfront examining where your network security is wanting, you’ll know what you need to ask from cybersecurity companies in your RFP.
In addition to vulnerabilities within your current systems, you’ll also want to pinpoint the assets that you need to protect.
Why does this matter?
Identifying potential threats and risks starts with taking inventory of all your digital assets that need protecting, such as data, applications, network infrastructure, and hardware. The most sensitive data will vary from client to client and may require different levels of effort to guard.
Assess the threat landscape by identifying current and emerging cyber threats that could put your assets at risk, including phishing attacks, ransomware, insider threats, and any industry-specific threats.
Identifying the potential threats and risks to the assets most critical to your mission will be essential to your overall budget allocations.
Prioritizing risks and threats based on severity helps determine where to focus your cybersecurity investments.
A vulnerability assessment uncovers weaknesses in systems, software, or processes that attackers could exploit. A formal risk assessment evaluates the likelihood and impact of each threat. Factor in legal obligations and compliance requirements, which can amplify the risk of noncompliance if threats aren't properly managed.
Understanding how these different risks could disrupt business operations, lead to financial loss, and/or damage reputation helps you with assigning the appropriate weight and prioritization to each threat. Taken together, these assessments guide your budget allocation towards the areas of highest risk and greatest importance to protect your organization.
Once you’ve determined a cybersecurity budget, you want to stay on budget. However, this can be easier said than done if priorities shift or your top-priority assets require more spend than originally planned. With stakeholder alignment and cost-effective, scalable security solutions, it’s possible to keep your budget on track. Here are some simple strategies for optimizing your cybersecurity spending:
Because the threat landscape is always changing and posing new threats to cybersecurity, your budget and collaborative efforts with outside companies should regularly be re-evaluated.
Conduct regular audits of your cyber vulnerabilities and needs to ensure that your work remains in alignment with your organization's changing security needs. Audits help to identify specific weaknesses in systems, processes, or policies to target fixes and focus your resources on the most critical needs.
Regular audits also help prevent costly security incidents. Instead of having to take reactive measures that can balloon your cybersecurity budget, you’re allotting for preventive security measures. After all, the cost of a security breach far exceeds the cost of regular audits and assessments.
Of course, any project will go more smoothly when management approves of its plans. This is especially important when creating a budget of any kind. So, a management or CFO figure will need to approve your cybersecurity.
While you may be an expert in the needs of the business, you may not fully understand the organization's constraints. Taking your budget to management will ensure you have the necessary support and resources to implement your cybersecurity measures effectively.
The presented budget and constraints will vary from company to company depending on the company's size, industry, and risk level. Alignment on budgeting from management is critical to make sure that your goals and allocations are realistic and can actually be carried out as envisioned.
Your cybersecurity spending should focus on prevention while also allotting the funds to resolve threats when a security incident happens. But that’s not all you need to budget for. Rather than focusing solely on immediate needs, build a strategy that supports long-term growth and resilience.
Maintaining while also improving your current security lays the groundwork for more advanced capabilities, stabilizing your security infrastructure and optimizing your spend in order to scale up. This approach ensures that today’s solutions don’t become tomorrow’s limitations.
Long-term security investments are about future-proofing your organization. These might include adopting advanced threat-detection platforms, AI-driven security tools, or building out cloud-based infrastructure. While these require more planning and resources, incorporating them into the budget over time allows you to scale strategically, keeping your security posture strong as your organization evolves.
We know that the cost of cybersecurity services can range dramatically and be difficult to justify the costs to management. It can be tempting to go with the cheapest options or allot for the barest security necessities. But remember, you get what you pay for.
Emphasize to management the high probability of cyber threats impacting your business and the costs for recovering from an attack. Then walk them through the security the organization needs and the variance in the cost of security services.
These are some of the many drivers that move the needle when it comes to cybersecurity pricing:
When it comes to cybersecurity, you can’t just “set it and forget it.” You have to keep up with evolving threats, and your budget will most likely need to evolve as well. Here are some steps to take, and budget for, to ensure you’re keeping your security up to date:
It’s easy to say that you want full-coverage solutions across all of your key assets, but it’s another thing to afford each and every protection. This is why budget allocations are so important — they dictate what we’re able to spend and where.
Once you highlight your assets, it’s time for an exercise. List your assets against the level of risk (how vulnerable they are) to your organization. In other words, which key assets pose more of a threat to your security than others?
Higher-risk assets that you deem crucial should be given the most funding in your cybersecurity budget. Whereas, assets with low-risk attributes can be given less funding because there’s less of a chance that a cybercriminal would breach that part of your system.
Not all of these allocations will be necessarily intuitive. If you’re not already, collaborate with your CISO and CFO to get an understanding of what’s possible within the confines of your budget.
Incident response is one area that every company hopes to avoid spending for.
Here are the ideal steps companies should take in response to a cyber incident:
In case of a real incident, the last thing you’ll want to do is waste time figuring out how to handle it. To establish a process that effectively addresses each of these steps, you’ll need to collaborate with in-house teammates and/or cybersecurity prevention professionals to create a plan.
Once you have an incident response plan, you can function with more certainty. For this reason, you’ll want to allocate part of your budget to response and recovery measures. These expenses can include incident response teams or disaster recovery plans.
This way, your organization is prepared to handle any security incidents.
Remember, not everything will go to plan in a cybersecurity project. That’s why it’s smart to set aside some extra budget for contingencies and unexpected costs. In this case, that might entail:
Additionally, your budget should be a living document. This means that you need to regularly review and update it to account for your changing needs and limitations for it to work. This will help you stay protected and within your allocated financial resources.
A cybersecurity budget will ensure your cybersecurity efforts' success and protect your business and its assets.
Small business owners need to prioritize cybersecurity and allocate resources accordingly, as even a small breach can have serious consequences.
By following a budgeting process that includes researching and comparing prices for different solutions and services, considering the ongoing costs of maintenance and updates, and allocating resources for training and education, small business owners can create a budget for cybersecurity services that meet their needs and helps their business succeed.
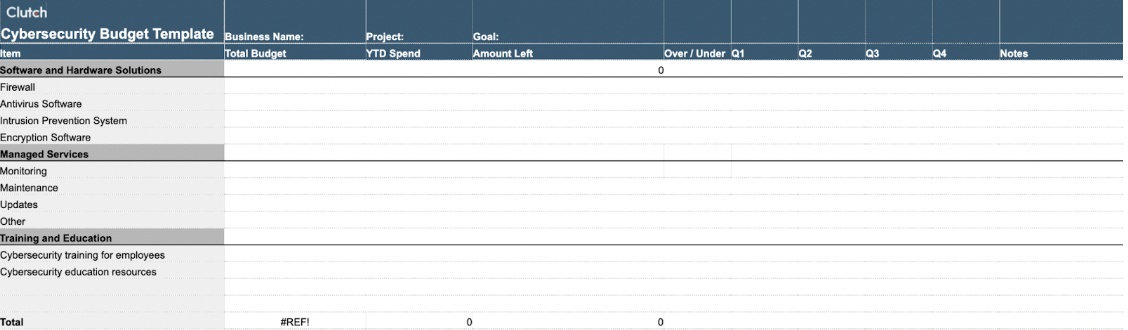
Download the Cybersecurity Budget Template
Need help implementing a cybersecurity plan? Connect with an expert cybersecurity team on Clutch.


