Updated May 8, 2025
Data is more precious — and vulnerable — than ever. Now that cybercriminals are shifting to AI, businesses must rethink how they protect what matters most.
Companies today collect and process unfathomable amounts of data: customer details, financial transactions, proprietary algorithms, employee records, and more. Artificial intelligence's (AI) growing use has only generated more data. Every model trained, every insight earned, and every automated process relies on the data you need to run your company. That makes your company an attractive target.
Data is currency for cybercriminals. With AI, they have brand new ways to snatch it — faster phishing, deepfake social engineering, automatic vulnerability scanning, and smarter malware. What used to require a coordinated group of hackers can now be pulled off by one person using AI they found on the dark web.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
One of the most high-profile recent examples was the cyberattack on MGM Resorts in 2023. Ransomware groups ALPHV and Scattered Spider used AI-enhanced social engineering to impersonate an employee on a help desk call. That single phone call allowed the attackers to overtake the company’s internal system.
Within hours, slot machines shut down, hotel keycards failed, reservation systems went dark, and MGM’s operations across Las Vegas and other properties ground to a halt. The damage incurred over the attack’s 10-day duration and the resulting fallout were so severe that the company reported a $100 million hit in Q3 earnings.
What made this different from earlier attacks? The speed and exactness of the AI-generated voice clone, the targeting of weak human links (like help desk workers), and the way the hackers simulated legitimate requests while raising almost no red flags contributed to how easily and smoothly this cybercrime was carried out, leaving MGM Resorts reeling.
We surveyed 250 professionals in the IT and cybersecurity industry to better understand the state of data security and what businesses are doing to safeguard their data and prevent operational breakdowns and data theft.
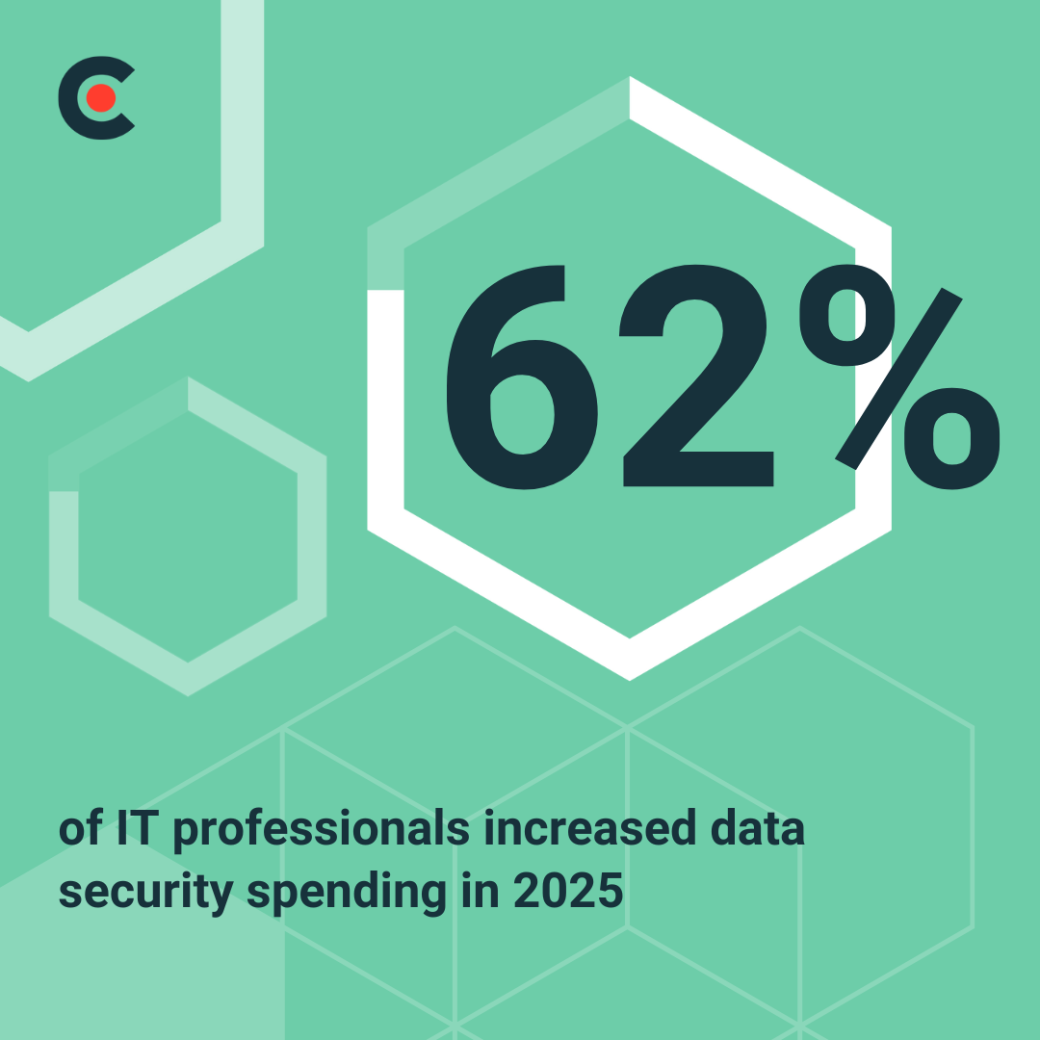
Our survey found that 62% of respondents increased data security spending in 2025, and with good reason — consumers are paying attention. They want to know you’re protecting their information, and one data breach can permanently shred the trust they once had for your company.
The financial fallout isn’t insignificant, either. Ransom payments, downtime, regulatory punishments, and PR cleanup can cost millions. Add attackers’ growing AI adoption, and a dangerous situation becomes a powder keg. Today’s threats are more nimble, shrewder, and harder to detect than ever.
Although AI makes business operations more efficient in many ways, it has also created new digital weaknesses. According to our survey, these are the top data security struggles companies face right now.
AI and machine learning (ML) models train on enormous datasets. As your business collects more information, it also expands its breach potential. Companies store confidential data across more systems than ever, making tracking, managing, and protecting it more complicated.
AI gives cybercriminals a whole new set of techniques, like deepfake phishing attempts, voice-clone schemes, and malware that can change on the fly. Their attacks usually mimic legitimate behavior, which makes them sneakier for conventional methods to catch. For IT personnel, keeping up requires new tools and faster reactions.
AI security requires specific knowledge, but experts trained in cybersecurity and AI’s ins and outs are rare. Many teams are under pressure to re-educate or expand — fast. Without skilled personnel, even state-of-the-art tools fall short of their security potential, and hackers can weasel through the gaps.
Small and midsize businesses (SMBs) aren’t sitting on their thumbs. Amidst growing threats, IT teams are rethinking how to protect sensitive information: updating their defenses, adopting smarter tools, and shoring up weak points before bad actors can break through them.
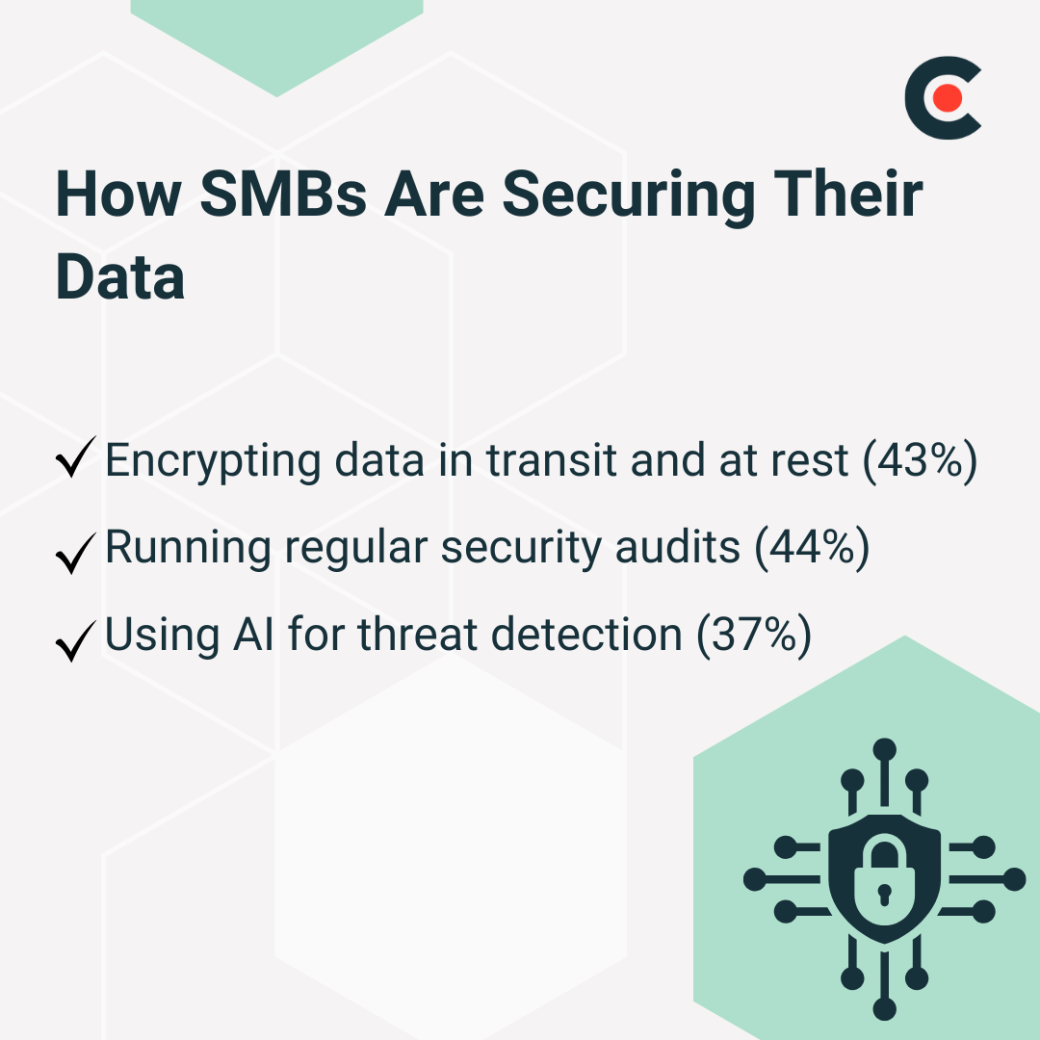
Here’s what our survey found SMBs are doing to guard their data.
Encryption is one of the most effective and widely adopted cybersecurity defenses. It protects data in two critical states: when it’s traveling between networks and when it’s stored long term.
Encryption protects data from interception during transfer and renders it useless to anyone who might try to grab it mid-transfer. Remote workers, third-party vendors, and cloud-based services especially need this safeguard, as what they send is vulnerable at any number of endpoints.
When data is at rest — sitting in a database, backup, or file storage system — encryption prevents unauthorized users from accessing it if those systems are ever breached. Without the encryption key, the data is gibberish. Beyond firewalls and controlled access, encryption is an essential security layer.
Encryption is an affordable and scalable way for SMBs to reduce risk. It helps your company comply with GDPR, HIPAA, CCPA (General Data Protection Regulation, the Health Insurance Portability and Accountability Act, and the California Consumer Privacy Act), and other relevant legislation.
Encryption also makes you more trustworthy in your customers’ eyes. Clients who know your company handles their information securely are more likely to stay loyal. While no single tool can block every cyberattack, encryption drastically limits the damage if one does get through.
Regular audits let you keep a pulse on your company’s security health. Cybersecurity threats change constantly, and systems that were secure a year ago might now have vulnerabilities. That’s why almost half of IT professionals now run audits regularly, not just after a security incident.
A comprehensive audit looks at everything:
These audits often uncover hidden risks, like employee accounts with more access than they need, outdated plugins in core applications, or sensitive information stored in the wrong place.
Security audits also help highlight training gaps. If employees consistently share their credentials or click suspicious links, that’s a red flag. With regular reviews, you can fine-tune your company’s technical defenses, policies, and employee education efforts.
For SMBs, auditing on a schedule turns cybersecurity from a reactive chore into a proactive habit. It prepares your company for external audits or regulatory inspections, which can cost you dearly if they reveal data protection lapses. The real value is long-term: habitual accountability that helps catch minor problems before they spiral into something far worse.
While AI powers these criminal infiltrations, it also helps targeted companies fight back. Nearly 40% of IT professionals now employ AI to detect unusual network activity.
Unlike conventional security systems, which depend on known attack signatures or manually defined rules, AI systems train on behavior. They build a baseline of what’s “normal” and throw alerts when something deviates, even if it doesn’t match any known threat.
Such aberrations might include:
AI threat-detection tools can catch many irregularities before they become breaches. They work 24/7 to spot signs of trouble while your human IT staff is off the clock.
AI gives SMBs with smaller IT budgets and teams a strategic advantage. It reduces time-wasting false alarms, letting your cybersecurity team focus on the real threats. Some platforms even offer automated responses, like temporarily locking accounts or blocking specific IP addresses until a human can review the situation.
As cyberthreats become more complicated and harder to spot, AI is taking on a bigger role in many defense strategies—not as a replacement for people but as a second set of eyes that sees what humans might miss.
More than half of the businesses we surveyed (56%) now either fully outsource their data security or have their internal IT staff collaborate with external specialists. For many SMBs, the dual-pronged approach is the best of both worlds: in-house oversight with outside expertise.
Outsourcing brings in specialists who live and breathe cybersecurity. They stay on top of new dangers, tools, and updated regulations that your internal team may not have the staffing or time to manage. They also use sophisticated defense technology and processes that might be too expensive or complex for smaller companies to implement independently.
Working with experts can also improve your incident response time, reduce the strain on your in-house staff, and shake up your company’s risk management perspective. When attacks evolve faster than your internal team can catch up, collaborating with specialists can mean the difference between a minor issue and a full-blown crisis.
Ultimately, outsourcing doesn’t mean ceding control; it means adding firepower. When your team works with outsourced experts, you get wider coverage, more innovative strategies, and a stronger chance of warding off cybercriminals.
AI has forever altered data security, but businesses are adapting fast. Encrypting data, running regular audits, embracing AI techniques, and tapping into external expertise allow you to shield your information — and your business — more effectively against cybercrime. The risks are real, but so are the tools and methods you need to defend your company’s data.