

Updated November 21, 2025
Between AI-driven cyberattacks, advanced persistent threats (APTs), and everyday bad actors, the cybersecurity landscape is becoming harder to manage each day. To address this need, 58% of businesses have used their in-house IT team to handle their cybersecurity processes, and 17% outsource to an MSP or cybersecurity provider.
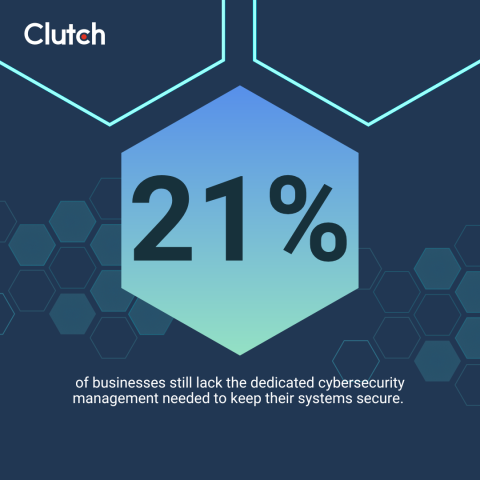
However, 21% of businesses still lack dedicated cybersecurity management needed to keep their systems secure.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
The need for additional cybersecurity expertise can be especially challenging for small- to-medium-sized businesses (SMBs). Even the smallest company can be subject to an attack, and one successful cyberattack could be enough to permanently shut down a small business.
This guide will look at the importance of cybersecurity for small businesses and some of the top small business cybersecurity solutions. We'll examine the main reasons that some businesses have yet to invest in cybersecurity, as well as key factors to consider as you weigh your cybersecurity options.
We'll also show you ways to build a robust cybersecurity infrastructure in your business, and how you can know when the right move is to hire a cybersecurity expert of your own.
SMBs and micro-businesses have fewer resources to devote to cybersecurity, and that makes them an easier target for threat actors. In fact, 58% of businesses with fewer than 200 employees have been the victim of a cyberattack in the last year.
Yet, while SMBs clearly face a greater vulnerability to cyberattacks, many haven’t invested in the resources needed to keep threat actors at bay.
Some reasons that SMBs have yet to invest in their cybersecurity infrastructure include:
Some may opt to focus on sales, operations, and growth instead of cybersecurity. This can be understandable when SMB owners face such a heavy workload. However, companies that hire a cybersecurity expert to strengthen their security posture often find that doing so increases their productivity.
Offloading your cybersecurity workflows to a managed services provider (MSP) frees up your team for more mission-critical tasks, letting you get back to growing your brand without worrying about a damaging breach.
While SMBs have reasons for hesitating to invest in cybersecurity, they must carefully consider the cost of failing to implement the right security measures. The cost of doing nothing can be far greater than the cost of developing a proactive cybersecurity strategy. Some factors for SMB owners to take into account are:
Between having so many entry points to cover and the high cost of failing to cover them all, the question shouldn't be if SMBs can afford to implement a cybersecurity infrastructure — it's if they can afford not to.
While adopting some form of small business cybersecurity is essential for their survival, companies must still find affordable solutions that align with their unique needs. These are a few affordable small business network security options that leaders can consider.
MSSPs are third-party cybersecurity experts that provide end-to-end monitoring, maintenance, and support for your network. Services that an MSSP can offer to SMBs include:
To provide these services, MSSPs use high-availability security operation centers (SOCs) located on their own sites or from other data center providers, enabling them to deliver 24/7 support to their clients. This reduces the amount of cybersecurity resources an SMB needs to hire, train, and retain in order to keep a strong security posture, making them a cost-effective alternative to assembling your own in-house team.
Putting into place basic best practices can go a long way toward helping companies strengthen their cybersecurity posture. A few simple steps that SMBs can take are:
Another key way to elevate your cybersecurity posture is to create periodic data backups and disaster recovery plans. Having up-to-date backups can reduce your downtime and help you maintain your business continuity in the event of a breach. Testing your recovery plan periodically helps ensure its effectiveness if you suffer a cyberattack.
Cloud providers offer many built-in cybersecurity protections, so leverage them to improve your network defenses. Each provider's exact features will vary, but common cloud security capabilities include:
Some cloud providers additionally offer tools to assist with regulatory compliance, helping reduce the risk of a costly fine. Assuring compliance also lets SMBs not only strengthen their data security but demonstrate their robust cybersecurity posture to vendors, business partners, customers, and regulators, elevating their brand image as a result.
Additional reading: ‘Cloud-Native Security Practices: How to Secure Modern Infrastructure at Scale.'
Even with the right small business cybersecurity solutions in place, taking the first steps in forming a comprehensive strategy can be a daunting task. You can get started by following these steps:
Communication is critical when responding to a cyberattack, so designate a team lead to direct your cybersecurity efforts. They may not be a fully trained cybersecurity specialist, but a good team lead should be able to maintain clear lines of communication with each member of your team and coordinate the many tasks associated with responding to a threat.
Today's cyber threats have become so sophisticated and scalable that no company can assume it's immune to attack. SMBs and micro-businesses have limited time, personnel, and resources to devote to cybersecurity, making them particularly vulnerable to a threat. But when a single incident could prove costly enough to end a business entirely, the cost of prevention is far less than the cost of recovery.
Some organizations may be able to manage their cybersecurity processes with their own IT teams in house, but others lack the experience needed to handle the additional burden. In such situations, offloading your cybersecurity operations can be a cost-effective way to strengthen your security posture and free up your team to focus on your core business processes.
Reach out today to connect with a cybersecurity partner that's right for you.


