Updated May 14, 2025
Internal cybersecurity projects rarely follow a straight path from start to finish. They are layered and packed with moving parts. Three areas, in particular, demand extra attention: migration, compliance, and testing.
Each of these steps plays a role in making sure your project not only gets done but gets done right. Migrations allow for a seamless transition of your data and systems, while compliance keeps you in line with regulations and internal policies. As for testing, it's your safety net to catch issues before they become problems.
The article below breaks down what IT leaders and teams need to tackle in each of these areas. It will equip you with the knowledge to create a solid cybersecurity project plan ready for real-world implementation.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
In a cybersecurity project plan, migration can mean a few things. You may be moving sensitive data to a more secure cloud environment or switching to a new infrastructure. Upgrading core systems like user authentication also counts as migration.
Regardless of its type, migration is a major moment in a cybersecurity project. If not handled properly, it can result in data loss and security breaches.
So, you need to start with a clear plan. It should highlight:
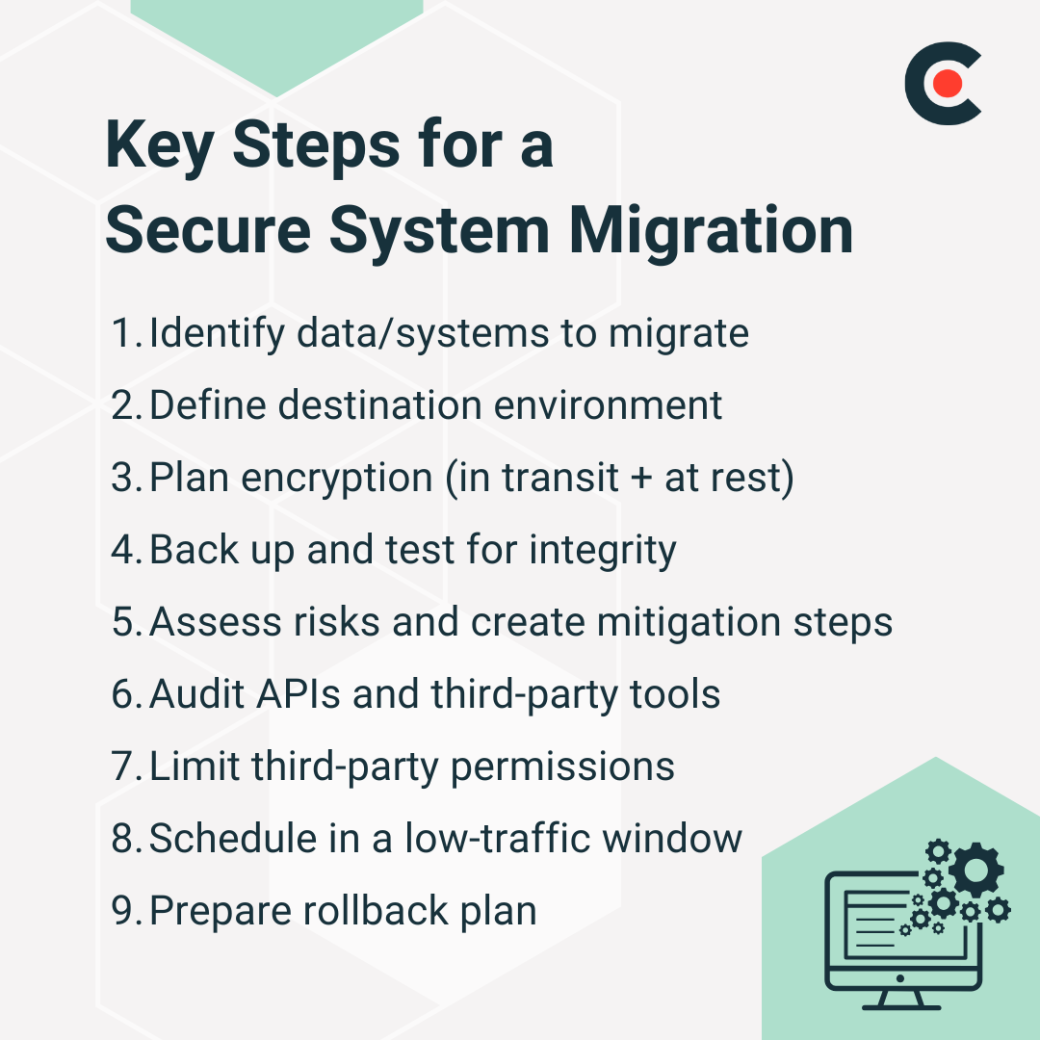
Prioritize data integrity during this process by performing backups and testing the systems once the migration is complete. Ideally, you want the data to arrive as it left, without corruption, loss, or unwanted exposure.
Encryption can be helpful in this regard. Encrypt your data in transit and at rest, especially if you're transferring regulated or sensitive information.
If your project involves APIs or third-party tools, audit them before moving forward. Not every integration is secure, so it may become a weak point that attackers can exploit. Use secure tokens and follow up-to-date authentication protocols.
Also, be careful about the permissions you grant to third-party tools. It's always better to limit access to only what is necessary for third-party actors to perform their designated function.
However, you should expect a few bumps, especially if you're dealing with legacy systems. These older environments may not play nicely with modern platforms, and trying to bolt on security as an afterthought wouldn't work.
Another potential hurdle is downtime. So, you should schedule migrations during low-traffic windows and have a rollback plan if things don't go as expected. Some good times to schedule migrations are on weekends, late at night, or early in the morning.
When working on a project, it's imperative to meet cybersecurity compliance requirements to avoid damaged reputations and lawsuits. The more regulated your industry is, the higher the compliance requirements.
Here are some ways to stay compliant during regular testing and system migration in cybersecurity projects.
Internal cybersecurity projects should start with an understanding of which rules apply. For example, it's HIPAA in healthcare, PCI DSS for payment systems, and GDPR or CCPA for personal information privacy.
These frameworks come with very specific requirements, and skipping over any part of them can open your organization up to serious penalties. In some cases, fines and penalties go up to millions of dollars. Other penalties include:
That's why it's important to loop in your legal and compliance teams right from the start. As Dmytro Sirant, CTO at OpsWorks Co., suggests, "Identify all security and compliance requirements as soon as possible. In regulated industries like healthcare and fintech, meeting HIPAA or PCI DSS is a must, so they have to be considered from day one."
Early collaboration saves time and helps you avoid missteps. It also gives your team a clear target to build toward.
Technology alone doesn't protect your organization. People do. If your team isn't trained, even the strongest security system falls apart.

As Serge Guzenko, CEO and Founder at WEZOM, explains, "Employee training plays a crucial role as human error remains the leading cause of cybersecurity incidents. Comprehensive, ongoing training empowers employees to identify threats such as phishing emails, social engineering tactics, malware attacks, and suspicious online activities."
However, don't just train them theoretically. Instead, put them in mock situations and teach them how to react appropriately.
Guzenko recommends, "Regular simulations and interactive training sessions not only boost cybersecurity awareness but also establish a security-conscious culture within the organization, significantly reducing vulnerabilities."
This way, employees know how to identify something suspicious and who to report it to. Over time, this builds awareness in your organization and teaches employees to be proactive in protecting sensitive information.
After the systems are in place, you need to test them. Put everything through the wringer to make sure it holds up under real-world pressure. It means simulating attacks and stress-testing performance to check for weak spots you may have missed.
Sirant shares that they "battle-test everything under load. Security audits, compliance checks, and performance validations ensure reliability before production rollout."
Here are the core security testing tasks every cybersecurity project plan should include:
These tests are not just a one-time thing but should be regularly conducted for continuous improvement and readiness.
Just because you've launched doesn't mean you're finished. In cybersecurity, threats evolve, and users can unknowingly create risks. Post-deployment monitoring helps you spot trouble early.
You'll want to keep an eye on things like:
If something goes wrong, which it eventually will, you must have a rehearsed incident response plan to deal with it. Your team should know exactly who does what and how to limit the damage quickly.
There's also a big difference between reactive and proactive monitoring. Reactive means scrambling to fix issues after they've caused problems. Proactive means identifying risks and addressing them before they become real threats.
Sirant suggests being proactive: "Set up a monitoring and incident response toolset. A proactive monitoring and response strategy minimizes downtime, detects anomalies early, and prevents small issues from escalating into major disruptions."
However, along with the plan, you should also offer training so your team knows how to use the tools effectively. As Gar Whaley, Co-Founder and CRO at Teal, advises, "After deployment, make sure to provide ongoing monitoring, end-user training, and structured support to address any issues that pop up."
Regular patching and vulnerability scans are also important. These measures protect against newly discovered vulnerabilities and keep your systems up to date with the latest security patches.
Security projects are iterative by nature. So, you should make room in your roadmap for improvements and updates.
Start by scheduling regular vulnerability reviews. These include reviewing newly discovered security risks, examining system performance, and gathering user feedback to spot friction points or unreported bugs.
Also, patches and updates should be scheduled on a regular basis. It's especially important to prioritize critical vulnerabilities, such as ones that could result in data breaches or compromise user privacy.
Don't forget to get input from your customer support team since they're often the first to hear about issues from end users. There should be a clear feedback loop between support, security, and development teams so that potential risks are caught early.
Not every company has a fully staffed cybersecurity team, and sometimes, even when they do, the teams might not have the most up-to-date expertise or sufficient resources. In instances like this, the smartest move is to bring in a dedicated cybersecurity agency.
Outsourcing cybersecurity services is a good option if your internal team lacks specialized expertise or if you need to move quickly. A reliable agency will work hand-in-hand with your IT team to secure your systems.
But how do you choose a reliable cybersecurity outsourcing partner? Guzenko says, "Clients should look for a cybersecurity partner who not only possesses strong expertise and relevant certifications (such as CISSP, CISA, CEH) but also demonstrates extensive practical experience addressing security threats specific to their industry."
Keep in mind that your outsourcing partner will not just help you implement cybersecurity projects but also maintain them.
So, Guzenko adds that "the partner should offer proactive monitoring, rapid incident response capabilities, and continuous updates and recommendations to keep the client resilient against emerging threats."
However, don't just focus on credentials. Look at how they communicate and whether they understand your company's compliance obligations and internal culture. A good partner not only brings technical skills but also aligns with your goals and values.
Transparency also matters. Even if the agency handles most of the work, your internal team should still have visibility into what's happening. Regular check-ins and shared documentation help keep everything running smoothly.
When you outsource, you don't hand off responsibility. Instead, you build the right kind of support around your team so your cybersecurity project plan can succeed.
Tools alone don't make a cybersecurity project successful. You also need to plan and follow through with rigorous execution.
From secure system migration to compliance research, employee training, testing, and ongoing monitoring, every piece helps protect your organization from risk. When internal resources are tight, a cybersecurity partner can fill in the gaps for you.
If you need assistance to guide your next project, check out our cybersecurity project checklist to tick every box.