

Updated December 16, 2024
Virtual private networking (VPN) is a powerful tool for telecommuting but is often mistaken for a “shield” that grants internet anonymity. While a VPN will not make you anonymous on the internet, it can make your browsing experience safer and more flexible. In the wake of COVID-19, VPNs can help businesses ensure data security as they encourage their employees to work from home.
A properly designed VPN allows for secure access to servers and data in your office or datacenter. Many businesses are already working from home, or are in late stages of building a work from home plan, to encourage employees to stay home during the COVID-19 outbreak.
A properly designed VPN allows servers to be accessed in the same way as if you are at the office, but there are a few things businesses should consider:
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
As a Sophos Certified Security Architect, I have deployed dozens of VPNs globally for Arium and have learned the best uses of the technology, and also its pitfalls, especially in the way users understand it.
While the encrypted tunnel created by a VPN does not necessarily create anonymity, it can help you access remote work resources, bypass location restrictions, and elude some basic targeted marketing.
The key component to all flavors of VPN is an encrypted tunnel. There are various types of encryption and tunneling protocols. You may recognize PPTP, L2TP, and OpenVPN from perusing the screens in your VPN software.
While VPN protocols work differently, they all accomplish the same thing: strongly encrypting traffic between source and destination. Assuming your encryption keys have not been compromised, the technology behind VPN is bulletproof.
“No snoops, hackers or even your internet service provider can see your location or data,” according to Forbes. The tunnel is secure whether the other end lies at a workplace, or a foreign server run by your VPN provider.
A point-to-point VPN is launched from a VPN client, or through the user’s operating system. It requires a username and password to connect. Some workplace VPNs also require a token or one-time password, usually generated from the user’s phone. A connection takes only a few seconds to establish.
Subscription VPN services have streamlined this connection process for simplicity. See the screenshot below from ExpressVPN, one of the larger subscription services.
The user simply chooses a location for the remote VPN server through which to route traffic and clicks the connect button. A username and password are still required but are saved for simplicity.
This differs from a corporate point-to-point VPN, where the user must authenticate each time for security.
Let’s say you trust your VPN company middleman with your identity. There’s still the issue of DNS leaking.
Every website on the internet has an IP address. Your computer needs the IP address in order to browse the website. It finds the IP address via a DNS server – which translates a human-readable address, say www.google.com, to an address readable by your system, say 8.8.8.8. If VPN is not configured properly, this DNS lookup happens outside of the VPN tunnel, completely within earshot of your internet service provider. Take the diagram below, for example.
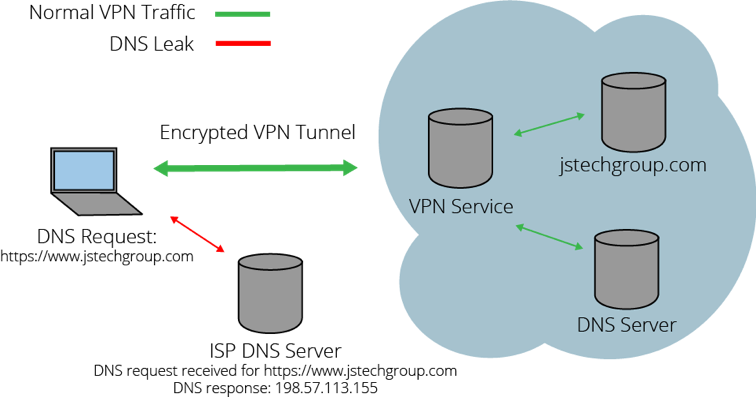
Even though your traffic is encrypted through the tunnel, your provider still sees which websites you are browsing, because DNS flows outside. The only way to keep your information out of your provider’s hands is to make sure all traffic flows through the VPN tunnel, including DNS traffic.
In a work environment, a DNS leak is less critical, because anonymity to your internet service provider is less in focus. Nevertheless, a good corporate IT department builds VPN routing to avoid this common pitfall.
With the weaknesses above, why use a VPN outside of a corporate setting?
Pushing traffic through somewhere distant has one key benefit – it looks like the traffic is coming from far away! When Netflix or other streaming services restrict certain content because of licensing, you can simply VPN tunnel to an area where the content is allowed.
Since your browsing looks to be coming from the remote server, not your location, you are allowed to browse and stream.
People in China have been using this same trick for years to get access to restricted information from behind the Great Firewall. A VPN is a useful tunnel for securely moving information.
How else is a VPN useful? While it can’t make you disappear, VPN tunneling eludes certain types of advertising - mainly those that track you by IP address.
Remember - you share a VPN server with hundreds of other customers. To advertisers, there’s no difference between your traffic and theirs. It’s like when two piles of laundry fall into one another – it becomes impossible to tell what belongs to whom.
Compare this with your direct internet connection, where all of your traffic comes from your IP address. There’s a certain level of anonymity in sharing your VPN provider’s servers with others. However, a VPN will not protect you from browser-based tracking.
“Ad networks generally use cookies instead of an IP address to identify you, so if you’re using a VPN to get away from ad tracking, you’ll be sorely disappointed,” says Lifehacker. Ultimately, VPN has more widespread implications in teleworking than in obscuring a user’s identity.
Virtually every Fortune 500 company tunnels employee traffic through its own VPN servers for security — and for good reason. A VPN allows an employer control of exactly how its remote workforce accesses the internet and its internal resources, at a small cost.
Like other VPN users, remote workers must establish the VPN tunnel the same as their anonymity-seeking counterparts. This is usually more complicated than clicking “GO,” often requiring a one-time password from a phone or authentication device.
And because of strict security requirements, a corporate VPN that’s idle may automatically disconnect, requiring the connection process to be repeated, over and over again.
The largest pitfall for a remote worker who regularly uses VPN is speed. Because of the encryption and extra routing steps required, a VPN can add significant time to browsing and downloads. Smart companies implement routing rules so that only traffic destined for corporate servers goes over the VPN. But many IT departments still send all traffic for safety.
If your corporate browsing is sometimes slow as molasses, your VPN may be to blame. Consider disconnecting when you are not accessing corporate resources, which prevents your employer from directly viewing your browsing.
VPN has strong use-cases in the secure transport of data. Like any tunnel, a VPN is only as secure as where it begins and ends. For remote access to workplace servers, VPN technology is ideal.
For home users, VPN makes traffic look like it is originating from elsewhere, which can circumvent location restrictions. This does not create full anonymity; your identity is known by the VPN provider. VPNs can also provide a small degree of protection against targeted advertising but are generally thwarted by tracking cookies, part of all browsing experiences.
If you need to implement a VPN for your home or office, it may be time to call a specialist.
Most IT consultants and network security specialists have access to the right network design tools to implement VPN in a secure way.
As a Sophos Certified Security Architect with years of experience in implementing VPN technology, I have witnessed its benefits firsthand.
Look for a specialist that can fully explain the flow of VPN traffic between sites, and takes precautions to maintain the security of encryption keys.
A tunnel is only as secure as its endpoints.


