

Updated January 3, 2025
Businesses have an ambivalent relationship with technology. While technology makes it possible for businesses to develop new products, automate processes, and keep costs down, it also makes them more susceptible to increasingly sophisticated cyberattacks.
The latest technology-based threats to business are deepfakes. The term “deepfake” comes from the combination of “deep learning” and “fake,” and it refers to images, audio, and video whose content has been altered by specialized algorithms.
The most common form of deepfake content are images where the face of a person has been seamlessly swapped with the likeness of another. A well-known deepfake is a video of the former U.S. President Barack Obama. The video portrays Obama giving a speech on the dangers of cybercrime. However, the speech was never actually recorded; it was artificially generated from separate video and audio footage.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
Deepfakes are the next logical step in the evolution of the fake image. What makes deepfakes different from photoshopped images and doctored video is the fact that they can be created with very little effort. This is possible thanks to generative adversarial networks (GANs). GANs are specialized machine learning systems that can create convincing image replicas based on provided data.
There are two phases involved in developing deepfakes. First is the training phase, which deals with the initial image manipulation.
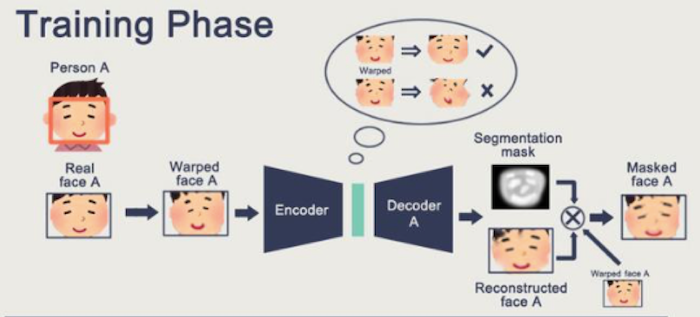
Source: GitHub
Then, the test phase begins, which involves the warped image with another image that produces the specific result the creator is looking for.
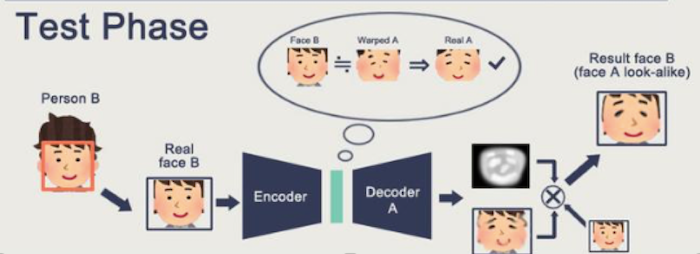
Source: GitHub
Although it doesn’t seem like it at first glance, there are a lot of steps involved in creating a deepfake. The ability to create fake images that are almost indistinguishable from real ones paves the way for new forms of cyberattack.
Deepfakes already pose a major threat for businesses, even though the technology is still in its infant stages. Because they are an emerging threat, there is no one countermeasure that can protect against all forms of this attack. Instead, there are procedures and techniques that can reduce the threat but not outright eliminate it.
Deepfakes have only been in existence since 2017, but they are already being used in several kinds of cyberattacks. Here are three attack scenarios that pose the most threat to businesses:
Phishing attacks rely on impersonation tactics to fool targets into divulging sensitive data, transferring funds, or opening the door for future attacks. Naturally, deepfake content makes it substantially easier to stage such attacks. Hackers can disguise themselves as C-suite individuals to perform whaling attacks, which is a form of phishing that aims to subvert high-ranking personnel within organizations.
On March 28, 2019, a group of three conmen used deepfake images to impersonate a French minister in order to scam a businessman into transferring 8 million euros to their bank account.
They recreated a fake version of the minister’s office and hired makeup artists to disguise themselves as high-ranking government personnel. These kinds of scenarios are likely to become even more common as deepfake technology develops.
Deepfakes can be used as a more subtle form of attack through influencing stock market prices. In these types of attacks, hackers will use digitally created images, audio, and video of industry leaders, politicians, and government officials to disseminate false information. If the fakes look convincing, this kind of activity can cause share prices to plummet or sore, depending on the agenda of the attackers.
So far, there haven’t been any confirmed stock market manipulation attacks using deepfakes, but since the technology is there, it is only a matter of time. We have already seen examples where public figures engage in activities that cause stock prices to drop. When Tesla CEO Elon Musk smoked marijuana on air in a podcast, Tesla’s shares dropped 6% in value.
Another potential threat from deepfakes is the increased likelihood and effectiveness of blackmail and extortion attempts against wealthy individuals. The ability to create fake audio and video allows hackers to create evidence in support of ongoing rumors or to start new ones. They can then leverage the fake evidence to force these individuals to fulfill their demands.
Even if the deepfakes in question were to be proven as fake, the speed at which they can be spread online makes it difficult to prevent their damaging effect. There are numerous instances of this happening already, most of them involving fake pornographic material with celebrity actresses. The authenticity of the deepfake is not relevant, as the damage can be caused instantaneously.
Deepfakes represent a fairly new form of cyberattack, so there are no definitive countermeasures against them. Various prevention tactics are being explored, including the three below:
One of the ways in which organizations could defend themselves from deepfake attacks would be to find a reliable way to detect them, preferably through automated technology. AI-powered detection software presents one such opportunity. In fact, the same deep learning algorithms that are used to create deepfakes can also be trained to find signs that an image or a video has been altered.
As seen below, in this step-by-step process, forensic analysis is involved to figure out what copy is authentic and what is manipulated.
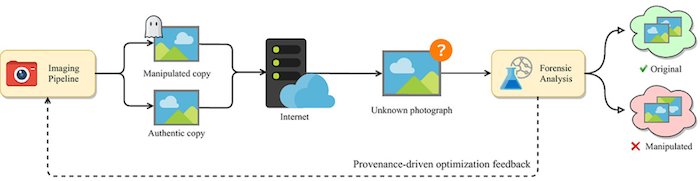
Source: Neuroscience News
This is just one of the many ways for users to detect deepfakes. Another tech-based approach involves watermarking content in order to detect tampering. For example, a cryptographic tool called Amber Authenticate can generate hashes at set intervals of a video. If someone alters the video, the hashes will change, warning the user the content has been modified.
Another approach to combating deepfakes is through the adoption of new security protocols in your organization. The likelihood that a deepfake will fool an individual is fairly high, but its ability to convince someone will drop sharply if more people are involved. By adding multiple checkups to scenarios where deepfakes might be involved, a company can sniff out the attack before it can do damage.
Hackers use deepfakes to make phone and video calls posing as company personnel. Therefore, in order to detect deepfakes, companies can establish security protocols that specify a checkup that procedure employees should follow when receiving such calls.
One of the reasons why deepfakes pose a danger to companies is the novelty of the threat. Most organizations are still unaware of what deepfakes are and what kind of damage they can cause. Conversely, companies can reduce the risk of succumbing to a deepfake attack by educating workers, management, and owners about the nature of the threat.
In order to develop a security-minded company culture, businesses need a systematic approach. Coaching employees about security risks and methods of prevention will make them more adept at detecting deepfakes.
Deepfakes can offer us a glimpse into the future of cybercrime. They are a prime example of how technology can mislead us into behaving in ways that can jeopardize the organizations we belong to.
And to make matters worse, the threat that deepfakes pose is still developing. Therefore, It is crucial that companies start preparing for deepfake attacks by educating their staff as well as integrating technological countermeasures as they become available. They can also hire a cybersecurity company if they need further help.


