

Updated January 2, 2025
In honor of Cybersecurity Awareness Month, Clutch interviewed information security experts at Fidelis Cybersecurity to help businesses better understand their cybersecurity risk profiles and how to build a better security perimeter.
Cybersecurity occupies a dark place in the public conscious. There are rarely (read: never) news stories that celebrate the strength of a company’s information security. Instead, we consistently hear about cybersecurity attacks, threats, and the failures of businesses in their attempts to respond.
Clutch spoke with Billy Cripe and Tim Roddy, the respective Vice Presidents of Global Marketing and Product for Fidelis CyberSecurity, a Maryland-based global cybersecurity company. They discussed how recent cyber attacks and the responses to them, particularly the Equifax breach that blew up in September, expose fundamental flaws in information security and shape the public’s dubious perception of cybersecurity.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
To Cripe and Roddy, the impact of cybersecurity simultaneously carries pain and gain. Companies suffer but (ideally) learn from their mistakes.
“The big, unfortunate piece about the headlines is that they haven’t been about innovation or forward progress. They’ve been about exploitation and harms and hacks,” said Billy Cripe, VP of Global Marketing for Fidelis Cybersecurity. “You never want organizations to have to learn their lessons by taking their lumps. That being said, learning still has to take place.”
The pain and gain associated with cybersecurity are unequal–there is much more pain than gain. However, the heightened awareness around cybersecurity caused by large-scale cybersecurity events provides an opening for businesses to make actual progress toward improving their cybersecurity.
This article explores four actions businesses can take to improve their cybersecurity using insights from Cripe and Roddy and Clutch's 2017 Cybersecurity Survey:
Use these four actions, and associated insight, to learn how to strengthen your business’s cybersecurity to combat an increasingly complex threat landscape.
Failures in cybersecurity start with the structure and framework of a business. Many businesses view cybersecurity as existing under the umbrella and function of IT, instead of as an independent, core business function.
"We want to burst the myths about cybersecurity as esoteric software in the IT silo. Cybersecurity is something that helps a business run, just like a CRM system is something that helps a sales operations systems run," said Cripe. "Similarly, cybersecurity needs to be in that same mindset as other sorts of business operation systems."
Your business should be prepared to respond to a cyber attack just as you would to an otherwise non-cyber related incident.
“Just like any large organization has a disaster preparedness plan and a crisis communication plan, a cyber attack response and communications plan are absolutely imperative,” said Cripe.
Businesses need to recognize the complexity of contemporary information security threats.
Businesses should view cyber threats as highly intelligent adversaries. An adversary takes advantage of security vulnerabilities and uses a multi-pronged approach to penetrate a business’ defenses.
“I’m not aware of any [victim of a cyber attack] that didn't have [defenses] in place,” said Tim Roddy, Head of Product at Fidelis Cybersecurity. “These adversaries are smart, talented, and well-educated. They’ll find a way in.”
One thing that makes these security adversaries so dangerous is that they currently outpace information security in the level of automation they use in their malware and attacks.
“The adversary is radically automated – they can create new variants of attacks, malware, and signatures, in microseconds through automation,” -Billy Cripe, VP of Global Marketing, Fidelis Cybersecurity
For businesses that have been victims of cyber attacks, simply having defenses is not enough for an adversary that possesses a high level of technical complexity.
Businesses need strong policies that recognize and address the mounting complexity of the information security threats and accounts for the internal security risk created by employees.
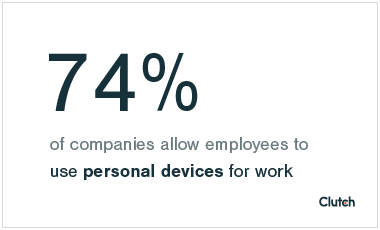
“Internal errors serve as vectors for entry. Internal threats that wreak havoc are usually driven by either a lack of training or awareness,” said Roddy.
The internal risk produced by a lack of training and awareness increases with an “expanding attack surface” that is created by the increased use of mobile networks and devices to access company data.
“When you talk about internal threats, there’s training, awareness, and understanding that needs to happen," said Cripe. At the end of the day, the most secure computer is one that is turned off and unplugged, but that’s not tenable. Consequently, really rigid or brittle policies are prone to fracture and fail.”
Effective cybersecurity policies incorporate training and communication to raise employee awareness of an automated adversary.
According to Clutch's survey, companies are making progress with training and communicating their cybersecurity policies. Communication, training, and compliance are the three largest areas of focus for implementing cybersecurity policy.
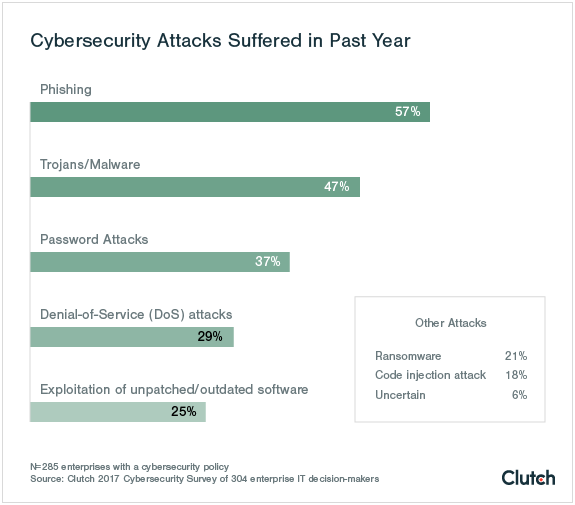
Cyber threats and attacks are a reality for every business. Even the best cybersecurity policy cannot prevent security attacks. 57% of companies experienced a phishing attack in the past year, while nearly half experienced a trojan or malware attack.
To account for the likelihood of cyber attacks, businesses need cybersecurity policies that include response protocols.
A cyber attack response plan should always be included in a cybersecurity policy. Well understood and practiced response protocols can ultimately determine the survival of your business after suffering a cyber attack.
To Cripe, the way to prepare for a cyber attack is by practicing how to respond and scaling response through automation.
“The ability to [simulate] a cyber attack is very important. A policy has to include the processes and ability for responding at scale...It’s a process that’s best when predefined and pre-practiced. In times of crises, we do what we’ve practiced.”
Processes for responding to a cyber attack include:
Businesses need to invest in automation to curb the cybersecurity “talent gap,” the term commonly applied to the current, and increasing, lack of capable human cybersecurity resources.
Cripe cites a global deficit of 3.5 million jobs in cybersecurity that will not be filled in the next five years. Given the lack of cybersecurity talent, companies need to turn to automation to help shore up their cybersecurity.
“There’s not enough people. The one thing that I believe will impact our industry over the next 10 years is automation. We believe that the way to transform security operations and to optimize them is with automated detection and response.”
Automation helps businesses to combat an advanced adversary by strengthening prevention and response to cyber attacks.
Although most cybersecurity awareness is a product of negative events, such as massive data breaches and hacks like Equifax, your business can use these negative experiences to learn and improve its policies.
Your business needs to:
Combine these four cybersecurity tactics and view them together as a single business process to strengthen cybersecurity on all fronts.


