

Updated January 3, 2025
The three categories of web application vulnerabilities – high-severity, medium-severity, and low-severity – often result from lapses in quality assurance in shorter development cycles.
Web application vulnerabilities pose a serious threat to your company's IT services and operations.
For the most part, web app vulnerabilities stem from programming errors that quality assurance (QA) engineers overlook during the software development and testing process or from continued use of open-source software components that are no longer patched or updated by their vendors.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
Web app vulnerabilities recently have become a more serious threat to companies.
Most companies now prioritize shorter software development and release cycles over web app quality and security. As a result, apps are now an easier target for hackers, who exploit vulnerabilities that your company or IT services company overlooked during the development process.
This article classifies the different types of web application security vulnerabilities, identifies the factors that cause them, and provides several tips to protect your company’s IT services infrastructure in 2018 and beyond.
There are three degrees of security vulnerabilities that affect enterprise and consumer-oriented web applications: high-severity, medium-severity, and low-severity.
High-severity vulnerabilities are security flaws that enable hackers to take complete control over a targeted application without having direct access to it.
Examples of high-severity vulnerabilities are below.
Cross-site scripting tricks browsers into interpreting and executing malicious JavaScript (JS) code to retrieve sensitive information from your cookie files. This enables hackers to impersonate legitimate users and access your corporate data including passwords and payment credentials.
An example of a cyber attack caused by a high-severity vulnerability is the infamous WannaCry attack of 2017 that infected over 200,000 computers in 150+ countries.
The malware associated with this attack exploited the Remote Code Execution vulnerabilities common for older versions of Windows.
Cross-site scripting was among the most common vulnerabilities of 2017.
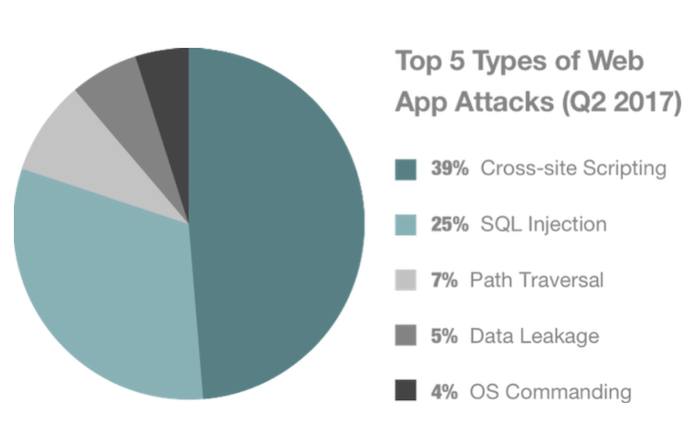
Source: PT Security
Other common forms of vulnerabilities are SQL injections (see below), path traversal, data leakage, and operating system (OS) commanding.
SQL injection vulnerabilities exist for websites and apps powered by Structured Query Language (SQL) database software. SQL software stores and organizes business data including customer records and payment info.
Although SQL databases require authentication, it is only implemented on the app level.
Thus, hackers who skip the authentication scheme of a web application can retrieve contents of an entire database. SQL injections accounted for 64% of web app attacks that were registered through 2016.
Remote code execution allows hackers to trigger code execution over the internet.
These attacks typically originate from one of your employees who clicks on an email link to a 3rd-party website. That website exploits the vulnerabilities of a web browser or the operating system (OS) running on your corporate computers and infects them with malware.
A hacker can then manipulate the malicious program over the Internet to access sensitive data or lock the computers and demand ransom. Ransomware attacks, for example, grew by 250% last year and caused over $5 billion in damage.
These vulnerabilities allow intruders to read directories and files outside the root directory, the top directory of a web app file system. During a file inclusion attack, access to any data stored “above” the root directory, for example, other websites’ directories, are inaccessible to users but are accessible to hackers.
Medium-severity flaws can partially compromise the confidentiality, integrity, and availability (CIA) of a website or web application. These flaws enable hackers to access business data and modify it to prevent your employees and customers from using it when needed.
Hackers take advantage of these vulnerabilities to launch Denial of Service (DoS) attacks and cause software downtime.
That is exactly what happened to Dyn, a US internet performance management company that suffered a major DoS attack in 2016. The cyberattack was triggered by the Mirai botnet, which infected Wi-Fi routers, surveillance cameras, and other connected devices. The botnet bombarded Dyn’s servers with traffic and brought down several prominent websites, including Twitter and Netflix.
Other types of “medium” security flaws include:
Unlike high-severity and medium-severity vulnerabilities, low-severity flaws cannot be exploited over a network and require authorized access or direct user involvement to take control over a web app.
Examples of low-severity vulnerabilities that can affect the CIA of your web application include:
As you can see, low-severity vulnerabilities are the easiest to avoid. Simple protective mechanisms like two-factor authentication (2FA) and diligent care for your company files can go a long way in preventing these vulnerabilities.
Security vulnerabilities arise from a few different factors, many of which result from failure to follow security best practices.
Common factors that compromise website and web application security include:
Neither software developers nor their customers want to reinvent the wheel every time they build a website or enable a new feature in a web application. As a result, the open-source software market is thriving.
The use of unpatched libraries and plugins, however, poses a serious threat to IT infrastructure security. Once a vendor stops rolling out security updates for a web app, hackers can freely exploit its documented vulnerabilities.
Take Java, for example, the No. 1 programming language for enterprise software development. Its unpatched third-party libraries, for instance, allow hackers to bypass firewall and connect to a company’s email servers through File Transfer Protocol (FTP) injections.
Although most security vulnerabilities stem from poor coding practices, programming languages and web app development frameworks are not created equal.
Drupal, for instance, is considered the most secure website content management system (CMS) on the market. It’s no wonder General Electric, Pfizer, and Qualcomm chose it over WordPress.
According to WP White Security, 70% of Alexa's Top 1 Million WordPress websites are vulnerable to hacker attacks due to the fact that anyone can create a WP plugin and upload it to the official store.
The easiest (and cheapest!) way to mitigate security risks is to devote more time to quality assurance and fixing bugs before an app goes into production.
With shorter software development and release cycles, however, developers have other priorities, which include on-time and on-budget project delivery.
In fact, 43% of software engineers admitted they had released apps with known vulnerabilities in the past, simply because flaw remediation would have pushed delivery dates into indefinite future.
The road to web security starts with a detailed blueprint of all the software assets you use.
2018 is going to be a turning point for all the companies that try to keep pace with technology. As more businesses invest in custom software development, embrace the fragmented and insecure internet of things, and allow employees to use personal gadgets in the workplace, we are all at a greater risk than ever.
Take the time to discuss your company’s IT services priorities or the web development company you choose for outsourcing your projects.
Here are a few things that should be on your agenda:
As a forward-thinking businessperson, you cannot be too serious about cybersecurity. After all, it can take up to 196 days to fix a critical vulnerability like SQL injection or Cross-Site Scripting once an attack actually takes place.


