

Updated December 18, 2024
Cloud application security is important in securing modern enterprises in today’s digital environment. Offering flexibility, scalability, and automatic security, it tailors to the needs of cloud environments. Utilizing this safeguard, organizations can avoid data breaches effectively and secure important virtual assets, making it suitable for compliance and development in the future.
Moving to cloud-native applications has become a vital tactic for organizations striving to improve flexibility and creativity. At the same time, such a shift highlights several cybersecurity issues that are difficult for conventional protection methods to address. As cyber threats evolve in severity and scope, investing in Cloud-Native Application Protection (CNAP) is a critical success factor.
CNAP protects microservices and container environments, integrating flawlessly with quick DevOps processes. Nearly 75% of enterprises use CNAPP solutions to protect their multi-cloud environment, indicating extensive use across industries.
This article explores why the adoption of CNAP entails more than fortifying enterprises, but a strategic change that provides modern enterprises a competitive edge amidst the cloud era.
Connect with industry-leading cybersecurity companies on Clutch. Use verified client ratings and reviews to find the perfect partner for your project.
A cloud-native application usually adopts a microservices architecture in which applications are broken down into self-sufficient and loosely coupled services that communicate through APIs. Although this technique increases the flexibility and scalability of applications, it leaves patterns for vulnerabilities. Every micro-service constitutes a potential target for attackers, and the safety of these endpoints is of utmost importance.
Further, there are dependencies across the services, and therefore, a faulty microservice can lead to cascading failure, potentially bringing down the entire application as other components are affected. Orchestration applications like Kubernetes often manage containers, creating other security vulnerabilities.
Containers encapsulate an application with all its dependencies within the limits of a single Object. A mistake in configuration may expose it to risks such as leaking information or allowing access to unauthorized individuals. In addition, the lifecycle of containers is very dynamic- they are constantly created and destroyed making it very hard to enforce effective security policies within the environment. Without adequate means, aggressors can take advantage of the existing security loopholes and cause data loss or suspension of operations.
DevOps practices cultivate an atmosphere that can rapidly adjust itself, and Continuous Integration/Continuous Deployment (CI/CD) pipelines quicken the development lifecycle. Still, the rate at which new applications are introduced is an index to let in weaknesses. External barriers to the development course are likely to be ignored, and the vulnerabilities will be discovered only during implementation.
While automated updates are time-saving, their installation can lead to danger without the necessary review procedures. New inclusions or updates may negatively impact previously secured areas and create new security risks. Therefore, organizations must integrate security into every phase of the CI/CD pipeline utilizing automated security screening that inspects and controls each phase of application release to protect the application.
Cloud-Native Application Protection (CNAP) is an advanced security framework for applications developed and operated in cloud-native environments. Given how businesses are migrating to architectures based on micro-services, APIs, and containers, conventional security methods are insufficient. CNAPP (Cloud-Native Application Protection Platform) meets these needs efficiently with a full range of security tools designed for a cloud-based environment.
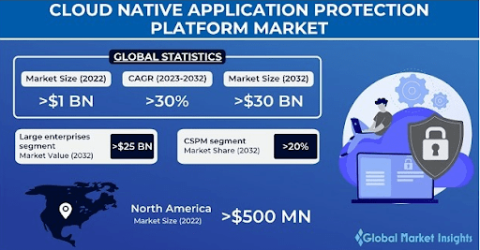
The Cloud Native Application Protection Platform (CNAPP) market was valued at approximately $1 billion in 2022 and is projected to grow at a robust CAGR of over 30% from 2023 to 2032. This growth is largely fueled by the increasing adoption of cloud-based solutions across various sectors.
Essentially, CNAP offers resilient security to containers, microservices, and APIs—the fundamental components of cloud-native applications—against cybersecurity threats. These components are highly distributed, making them vulnerable to various attacks. Cloud-Native Application Protection ensures that every service is properly secured and equipped with robust protective measures against potential threats.
In addition, the CNAP system incorporates ongoing surveillance and threat assessment to protect cloud-native applications. Because CNAP continuously monitors both container workloads and microservices, it can interrupt suspicious activities immediately, reducing response times and averting potential breaches.
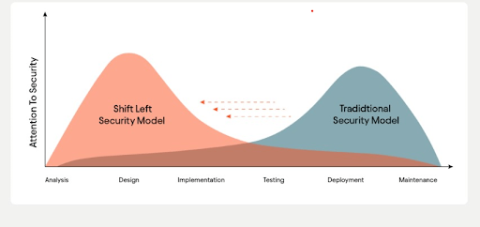
CNAP is different from conventional security models because it provides integrated security rather than a typical add-on approach. IDC surveys that the major factor that drives the increasing uptake of CNAPP is the shift-left model that integrates protective measures directly into the development process. In contrast, traditional security measures are mostly implemented when an application has already been developed, exposing various components to risks. CNAP is implemented throughout the entire build and lifecycle, ensuring that security is prioritized.
Furthermore, CNAP allows smooth communication with cloud-native components, helping in further versatility as compared to the older systems. Conventional security models are not built to protect dynamic, scalable environments like those in the cloud. Cloud-Native Application Protection Platform fills this gap as it is flexible and offers dynamic protection as your cloud architecture evolves.
With organizations moving towards a more cloud-native environment, taking up Cloud-Native Application Protection (CNAP) has become an important way of ensuring security. These are the most significant advantages of CNAP:
CNAP has the substantial strength of a powerful proactive risk assessment system. It allows for enhancing security and development synergy by identifying and mitigating risks at the development stage and averting any possible vectors. This possibility is improved by the capability to manage and eliminate the risk of any threats even while they are building up. This anticipatory tactical integration raises security further and fosters a defensive and flexible attitude in DevOps teams.
The workloads in a cloud environment are likely to change dramatically within short periods. As designed, CNAP is oriented toward the changing requirements of the organization and gears up to this demand; such flexibility ensures that protective features remain effective no matter the changes in application, architecture, or implementation approach. Also, CNAP works alongside DevOps activity and this understanding allows security to move with the complicated development and deployment processes. Such enterprise-level flexibility allows organizations to create ideas faster without compromising their safety.
Implementing CNAP is financially beneficial to organizations, this is because the amount of data loss and costs of data recovery are reduced since breaches are prevented and downtimes are limited. CNAP improves the efficiency of security management by allowing teams to incorporate security into the workflow without restraining their innovativeness. This efficiency makes it possible to use resources and productive capacity better, making CNAP a smart investment for forward-thinking organizations.
The increasingly strict regulatory mandates make CNAP a critical solution to enabling enterprises to comply with such requirements. Organizations can be compliant with industry regulations such as GDPR, and HIPAA by employing the most secure security measures. This reduces the chances of being penalized legally and develops trust among customers and other stakeholder parties.
When considering a Cloud-Native Application Security Platform (CNAPP), look for tools that have full coverage of the security of containers, microservices, and APIs. Gartner’s 2024 business report emphasizes the advantages of CNAPP implementation, underlining its part in enhancing visibility, reducing security threats, and improving cloud security.
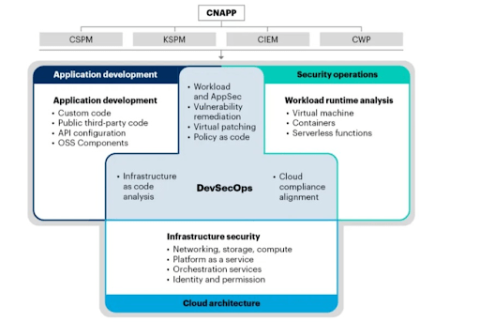
Technologies that perform important functions such as threat detection, automated exposure management, and seamless integration with DevOps pipelines should be taken into consideration. Very popular CNAP solutions such as Prisma Cloud, Aqua Security, and Sysdig have these solutions available and can be customized to different needs.
Conduct a cost-benefit analysis and ensure that the selected solution is compatible with the current system. In addition, analyze any other external factors such as regulations for finance or healthcare, an appropriate evaluation will confirm that the CNAP solution you have chosen meets the security needs of your application and does not go against your workflow processes.
To integrate CNAP successfully, embed this solution into your current DevOps and CI/CD practices. As a first step, automate security scans in the deployment pipeline ensuring they run concurrently with code releases without causing delay. Set expectations on when and how these scans would happen and ensure collaboration between DevOps and security teams.
As you work toward the integration, be on guard for potential challenges such as resistance to change or operational inefficiency. Let such concerns be addressed with piloting programs that showcase how CNAP can make operations secure, but not at the expense of productivity. Encouraging the adoption of DevSecOps, that is, including security considerations right from the start to the end of project development promotes teamwork, making security a collective responsibility.
A security-first mindset among employees is crucial for the successful implementation of CNAP. Periodical classes about cloud-native attacks, secure coding practices, and the importance of security in the development lifecycle will help in raising awareness. Think about specific programs or workshops that implement fieldwork and scenario-based training to fully involve participants.
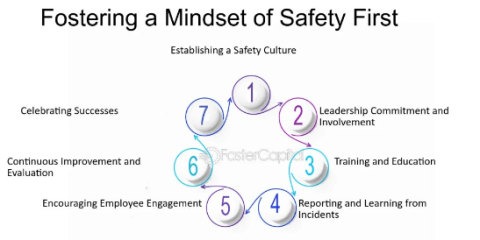
No culture can be nurtured without leadership buy-in hence management needs to embrace a culture of security at all levels of the organization. There should also be an incorporation of educational programs on a sustained basis for security awareness. Gamification techniques or reward mechanisms can be utilized to make employees more proactive with security measures and acknowledge personnel who work towards the security of the organization.
Enterprises can protect cloud-native environments against threats through the effective implementation of CNAP by selecting appropriate tools, integrating security into the processes, and cultivating security awareness. This Holistic approach not only addresses the issue of security but empowers organizations to embark on the business of cloud computing without any hindrance.
Investing in Cloud-Native Application Protection is not just a defensive measure: it is a proactive strategy that aims to prepare modern organizations ahead of the curve. By making CNAP a priority, organizations will improve their security level, streamline regulatory adherence, and promote innovation—all while maintaining the agility needed to stay ahead of emerging threats. As business continues to be transformed by the cloud, organizations that integrate CNAP into their operations will be best poised for continuous development in a more sophisticated digital environment.
Favour Efeoghene is a Digital Content Strategist specializing in crafting compelling narratives with innovative techniques. My work has been featured on Dzone, Hackernoon, Data Floq, and other authoritative publications, where I focus on delivering impactful and insightful content that bridges technology and real-world applications.


