

Updated January 2, 2025
Employees follow cybersecurity best practices, even beyond the boundaries of their companies' cybersecurity policies. But, when companies don't communicate their security policies or when their policies interfere with modern work processes, employees engage in risky behavior.
Over half of employees recognize that their company has a cybersecurity policy.
However, being subject to a company’s cybersecurity policy does not guarantee that employees follow it.
Looking for a IT Services agency?
Compare our list of top IT Services companies near you
Clutch surveyed 1,000 full-time employees to learn how they engage and follow through with cybersecurity policies.
We found that employees implement basic IT services and security initiatives like updating their passwords. However, many lack nuanced understanding about how their actions align with security policy and best practices or the impact they have on company security.
This report reveals how employees follow through on their companies’ cybersecurity policies and suggests steps businesses can take to improve employee recognition and compliance with security best practices.
Employees encounter their companies’ cybersecurity policies mainly through reminders and restrictions.
Employees most commonly interact with their companies’ security policies through password update reminders (67%).
Additionally, over half encounter internet restrictions (55%) and user permission prompts (53%).
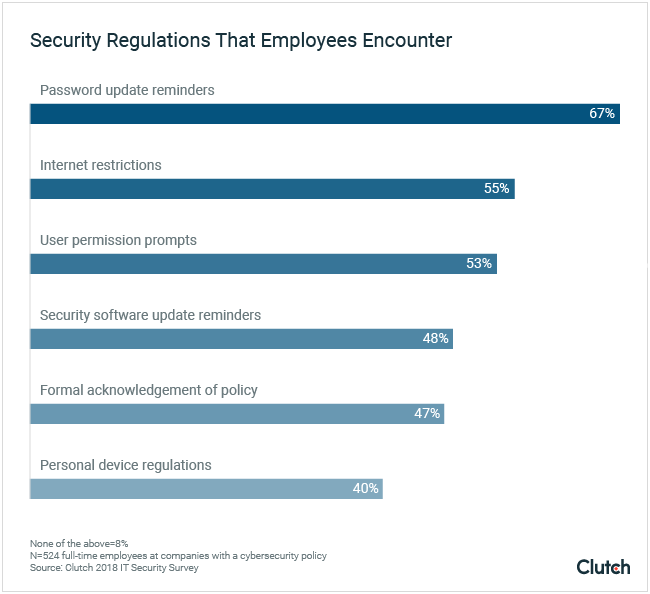
Less than half (47%) of employees formally acknowledge their company’s policy. This is less than the 52% who acknowledge that their company has a cybersecurity policy in place.
This means that some employees know their company has a policy, but their companies do not formally introduce the policy or how to comply with it.
Randy Battat, CEO of PreVeil, a company that offers encrypted email and file sharing to enterprises, explains that companies often fail to communicate policies throughout their ranks.
“Often, formal cybersecurity policies that are at the board and/or C-level, may not necessarily be propagated to every single employee,” Battat said.
If companies do not communicate their cybersecurity policies, such as requirements to update account passwords every 6-months, employees have a hard time recognizing when or how they are supposed to comply.
It can be difficult for employees to accurately self-report their compliance with their companies’ security policies.
As a result, some employees report acting in a security-oriented manner outside the parameters of their companies’ policies.
For example, over three-fourths (76%) use password protection techniques, which is more than the 67% who encounter password update reminders that are part of their company policy.
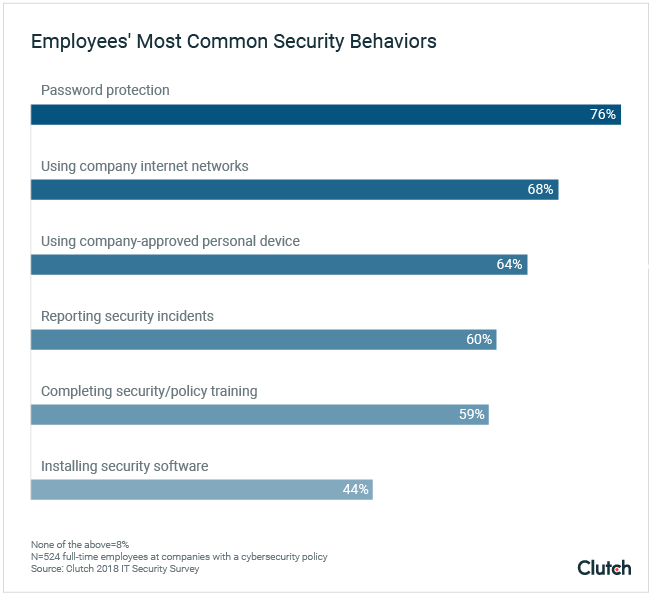
The discrepancy between the number of employees that encounter and use password protection illustrates a lack of communication about cybersecurity between companies and their employees.
It’s likely that some employees are subject to password restrictions or guidelines but are simply unaware of it. So, even if they use password protection, they may not be doing so according to policy.
Lack of policy recognition and policy are essentially the same in the context of cybersecurity. That is, if a company’s employees don’t realize a policy is present, it is essentially nonexistent.
Passwords represent the primary method of cybersecurity for employees. Employees engage with password update reminders more than any other element of cybersecurity policies, while password protection methods are the most common aspect of policies that they follow.
Most employees (82%) take the simplest approach to password protection by updating their passwords regularly.

Only a minority implement more complex forms of password protection. These methods include:
Passwords are the most common form of employee cybersecurity because they are simply the easiest for employees to master.
Updating passwords requires very little effort, and most employees are accustomed to password maintenance.
“[Employees] get the fact that they have to change their password regularly because it’s an obvious protection. There’s an obvious responsibility about that at an individual level,” said Steve Scott-Douglas, CIO of Ciklum, a software engineering and solutions company.
However, Scott-Douglas raises the issue that password protection is sometimes embraced superficially.
“You do wonder sometimes when you see people write down their passwords on their desk and leave it there if they are grasping its importance,” he said.
It’s encouraging that password updates are a common security practice. However, storing passwords where anyone can find them significantly undermines their effectiveness.
Employees download and install security software much less than IT decision-makers hope when they create policies for their companies.
Previous Clutch research shows that security software is part of 84% of companies’ cybersecurity policies, according to IT decision-makers.
This survey finds that employees are relatively unlikely to install and update security software. Less than half (48%) of employees receive security software installment reminders. Only 44% follow through and install security software.
Even if all 48% of employees who encounter security software followed through, over half would still lack updated security software.
The gap between how decision-makers design policy and how employees enact it underscores the importance of effectively communicating cybersecurity policy to employees.
If employees do not receive or engage with IT security services like software update reminders, those aspects of the policy are ineffective, regardless of whether they are formally established.
Personal devices pose a major security threat to companies when employees use them for work purposes.
Nearly two-thirds (64%) of employees use a company-approved personal device for work. However, less than half (40%) of employees are subject to regulations for their personal devices.
The act of using personal devices is not dangerous. It’s how employees most commonly use them that poses security risks.
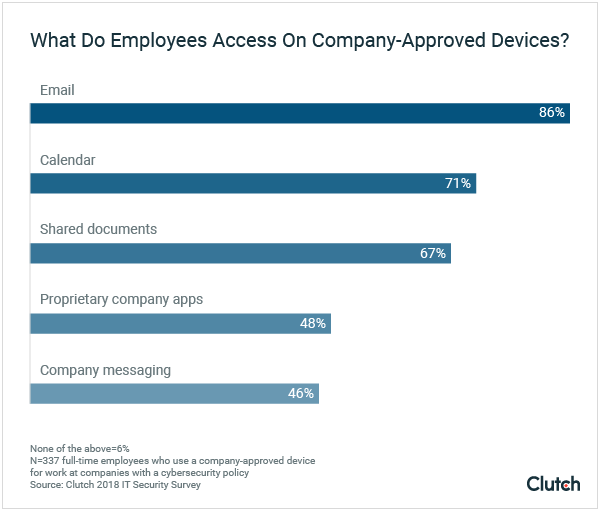
Most employees (86%) access their email using their company devices, and over two-thirds (67%) access shared documents.
Ron Winward, security evangelist for Radware, a global security company headquartered outside New York, explains that in a modern workforce, employees expect to use their personal devices for work.
“The reality is that people expect to be able to bring their own devices and use company resources for personal use. They expect the freedom to do this, and network operators typically allow it,” Winward said.
Because employees use their devices as part of their normal work activities and processes, companies should set realistic expectations about the safest ways to use them.
Doing so affords companies the opportunity to educate their employees about the impact devices can have on company security.
The risks that employees take by using a personal device for work are typically not because they intentionally open a sketchy email.
Instead, ostensibly “normal” communications and shared documents open the door for access to your entire company system if they fall into the wrong hands.
Battat explains that security-sensitive communication rarely includes an explicit label that reveals its security risk.
“We've seen that at many companies, employees believe that information that needs to be protected is special, sensitive stuff that's explicitly marked, and most of the everyday communications they receive and send aren't a risk for their organizations,” he said. “The reality is that the majority of communications, and the majority of an organization's intellectual capital, can be found in the ‘ordinary’ email or shared file.”
In the modern workforce, activities, such as accessing emails and shared documents on a personal device, are so normalized that employees lose sight of their potential security risk.
In particular, the easy access to company information that companies have across various platforms and devices accentuates this risk.
Ease of accessibility reduces employees' ability to recognize data as important or sensitive, according to Steph Charbonneau, CTO of TITUS, a company that specializes in data protection.
“[Employees] work across platforms, devices, and productivity tools. They need to know the business value of the information they’re handling on a regular basis so data protection can happen within the flow of work,” said Charbonneau.
Companies can reduce risk if they train their employees about what information is sensitive to their organization and how to securely access it.
Companies should implement IT security training for all employees. If designed with the goal to reduce security vulnerability, IT security training helps ensure employees operate in a secure manner.
Winward identifies developing a clear IT security policy and educating employees as the foremost priority for companies looking to improve their security, especially if companies approach it in a constructive manner.
“The best thing you can do is educate your employees on security best practices, and what they should do if something seems suspicious,” said Winward. “Be approachable so that they don’t want to hide an event from you out of fear.”
If employees feel comfortable approaching their companies about security issues, they are more likely to do so. However, employees may hesitate to engage decision-makers if they fear retribution.
Training employees to follow security policy or recognize sensitive IT services and data is more effective if it is consistent.
Currently, more employees (60%) report security incidents than the number that completes security or policy training (59%).
This discrepancy indicates that employees generally understand and recognize a dangerous scenario even without explicit direction or training.
However, among employees who experience cybersecurity training, 52% say it occurs only once a year.
Running annual security training means that companies are only going through the motions with regards to cybersecurity, according to Terence Goggin, Specialist Leader at Deloitte.
“Many regulatory cybersecurity/cyber-risk frameworks require that all employees receive cybersecurity awareness training on an annual basis, but it's clear that's not sufficient,” said Goggin.
Instead of formulaic, annual training, companies should develop consistent cybersecurity training that employees encounter regularly.
In addition to consistent training, companies should design cybersecurity policies to address common employee obstacles, like overbearing or tedious login credentials.
Employees' cybersecurity behaviors do not align completely with elements of their companies’ policies that they regularly encounter.
In fact, employees exhibit secure behavior that extends beyond their companies’ policies. For example, more report security incidents than receive policy or compliance training.
In addition, more employees use some method of password protection than those that receive password update reminders from their companies.
Employees consider passwords the primary form of cybersecurity. It is both the element of their company's policies that they encounter most and the cybersecurity behavior they are most likely to exhibit.
However, employees undermine their companies’ security through lax or misinformed security behaviors, like writing passwords on their desk or using personal devices to access email and shared documents.
These actions represent gateways that put sensitive company information at risk.
Overall, companies' cybersecurity policies should reflect modern worker mentalities and emphasize consistent training and compliance to ensure employees are not security liabilities to their companies.
Clutch surveyed 1,000 full-time employees about how they interact with cybersecurity policies at their companies.
Less than two-thirds of employees (65%) work at companies with over 50 employees. Over one-quarter (26%) work at companies with over 1,000 employees.
Nearly half (45%) of employees surveyed hold a manager-level position or higher. A similar number (40%) are associates, and 15% are at the entry-level.


