Updated January 3, 2025
Although collecting website visitors' information can yield valuable insights for businesses, strong security measures are needed to ensure that visitors' privacy remains protected.
There’s room for improvement when it comes to how website managers secure their sites and protect Internet users’ privacy.
When Internet users visit a site, they freely share information about themselves by making purchases, signing up for newsletters, or agreeing to terms and conditions.
Looking for a Web Design agency?
Compare our list of top Web Design companies near you
For anyone managing a website, the information site visitors leave behind can be a valuable analytic. But, 63% of website managers admit that they do not currently use common security features..
As you consider website improvements, what steps have you taken to evaluate how you are protecting your site visitors’ privacy?
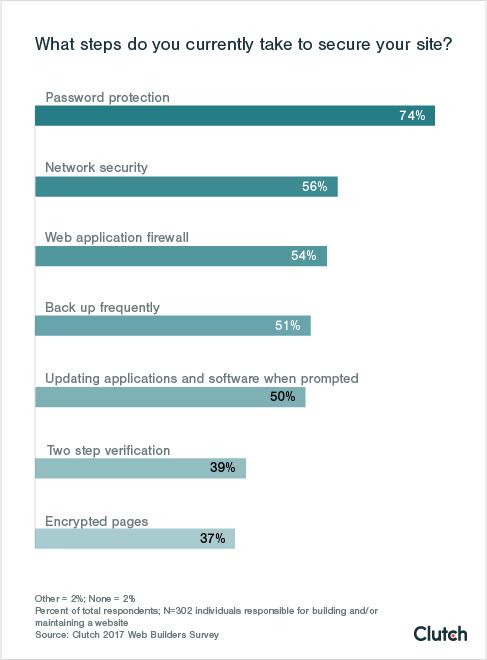
In a survey of 302 website managers, Clutch identified the steps website managers take to secure their websites, as well as how commonly used security measures can be applied to protecting website visitors’ privacy.
We use these findings to walk you through how to begin implementing security measures on your website that protect visitors’ privacy.
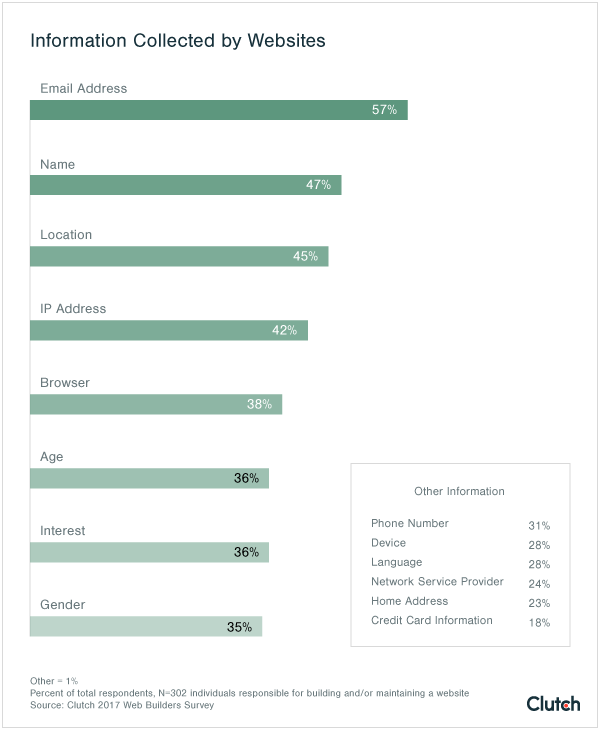
Email addresses are the most commonly collected information from website visitors. But, this information, when in the wrong hands, has the potential to cause the most damage.
Nearly 60% of website managers surveyed report that they collect email addresses. This is not surprising, given how often site visitors use their email to sign into an account or sign up for an email newsletter.
Idan Udi Edry, CEO of Trustifi, a company specializing in email transaction data security and privacy, believes an email address is one of the most dangerous pieces of information to share.
“When data is correlated over multiple web services, whether that is a Gmail account, a bank account, a password retrieval from Facebook, family-oriented documents, travel-agency information, and so on, it is done through the email address,” said Edry.
Internet users share their email address regularly to sign-in to different accounts online. The practice creates a thread for hackers to tug, unraveling much of their Internet presence.
For example, a hacker who manages to steal a company’s list of email newsletter recipients may be able to work through Gmail accounts, testing weak and common passwords to see which he or she can crack. Once a hacker has gained access to an email account, it could yield everything from sensitive financial information to private medical details that could be used to harm the user.
Other commonly collected pieces of information include name (47%), location (45%), and IP address (42%), a unique code that identifies each device using the Internet.
In the United States, it’s largely up to private companies to ensure that users are protected appropriately, but the UK’s 1998 Data Protection Act established guidelines that may serve as a helpful starting point in determining a strategy for your organization.
Site visitors may not be aware that your website is collecting their information, so it’s important to maintain trust by taking the necessary steps to protect user data.
The first step to securing the information your website collects is conducting an audit of the information you already have.
Although some pieces of information, such as a site visitor’s date of birth, may seem benign, given how commonly we use birthdays in passwords, it may have larger implications.
Think like a hacker by asking yourself:
For example, if your website collects visitors’ credit card numbers, home addresses, and email addresses, a successful hacker may be able to make unauthorized purchases with stolen information.
Take a closer look at the question, “What could a hacker potentially guess if they obtained this information?” Edry compares the threat posed by a hacker in possession of an email address versus an IP address. He points out that a typical hacker can figure out a user’s IP address, plus some details about the infrastructure behind it, with little effort. But learning anything else would require more work.
On the other hand, an email address gives a hacker access to more information.
“With an email address, [a hacker] won’t have to work a lot in order to retrieve privacy information,” Edry pointed out. “The combination between [an email address] and a name is enough to start the reconnaissance on someone as a user.”
And, if you think about what websites might have your email address on file, it seems like every new user account requires an email address.
Depending on where your organization is located, there may also be legal dimensions to protecting your users’ privacy.
By identifying the information that makes it easier for a hacker to crack other accounts, you can prioritize what information you should encrypt on your website. (Encryption is a process that translates data on your website into a code that renders it useless to anyone who attempts to hack in.)
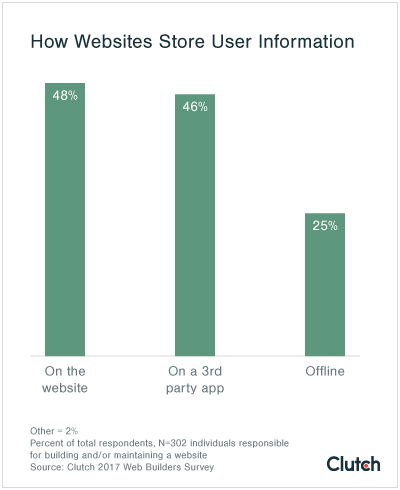
Once website visitors’ data has been collected, 48% of website managers store the information on their website; 46% store information on a third party app, such as Dropbox, and 25% store information offline.
Michael Tys is a mobile developer at TechMagic, a mobile app and web development studio based in Ukraine. He points out that even the Romans used simple methods of encryption by putting sensitive messages into secret codes.
“From my point of view, security approaches should not bring any complication to a user,” said Tys.
However, when it comes to encrypting information stored in the cloud, there is an added complication when multiple users need to access encrypted information. “Here, the ‘magic’ takes place,” said Tys. Each user is associated with a key that is used to decode the data; unlike passwords, keys are recognized on the operating system level, rather than functioning as passwords users must type in.
“From the science side, it is not magic—just a combination of mathematical operations applied to the keys,” said Tys.
The good news for website visitors is that implementation of encryption, while still below 50%, appears to be increasing. About 40% of website managers report that they already have encryption in place, and 21% plan to encrypt information in 2017.
Depending on your operating system and the amount of information you need to encrypt, there are numerous tools available:
PCMag also created a matrix that compares these popular tools by cost and capabilities. Remember to also encrypt any backups of your data and to store the password to your encrypted files offline in a safe place.
For more detailed information on encryption, including a step-by-step guide to encrypting sensitive information on your computer, we recommend Lifehacker’s “Beginner’s Guide to Encryption.”
Despite the availability of these tools, Tys believes a key obstacle to better security is simply poor user experience.
“The user is required to do a lot of things–provide your password, your cat’s name, the street you’re living on, your favorite number,” said Tys.
Looking ahead, Tys is most interested in the growing opportunities to use a fingerprint in place of a password on mobile devices.
“It’s a really awesome feature,” he said. “I’m using it on my banking application, and I can’t wait until the API is opened.”
Until then, encryption is an effective and reliable method for improving security and protecting website visitors’ privacy.
Evaluate where you are storing information to make sure the security features effectively protect site visitors’ data.
Nearly half (47%) of website managers self-host their websites. This option allows them a greater level of control over their security and privacy, but it typically requires greater staff and physical resources.

Meanwhile, 49% of website managers report that their websites are housed on servers managed by a third party, such as a DIY website builder or a service, such as Hostgator.
Edry points out that different organizations’ security needs vary depending on the type and level of user information they collect.
In some cases, a third party server, used in combination with other robust security features, may be an appropriate solution.
“In the end, whatever we call ‘the cloud’ is actually someone else’s server,” said Edry. “Whether it’s Amazon Web Services, Azure or Google, everyone is talking about the cloud, even though, at the end of the day, it’s nothing else but servers belonging to a different person.”
However, Edry points out that website managers should still actively evaluate whether the privacy and security features used by third party servers are sufficient. The key is to be intentional about choosing a server that meets your company’s specific privacy needs.
Depending on your website, your comfort level, and the nature of the information you collect, you can make an informed decision about the level of security you need.
Edry compares the process of choosing a level of security to buying a house: “You can buy a camera system or alarm for it ... or put a 24/7 guard at your front door,” he said. “It all depends on the level of security you want.”
By encrypting risky personal information and monitoring your servers, you can take two key steps toward safeguarding your users’ information.
Clutch surveyed 302 website managers responsible for building, maintaining, or building and maintaining a website for personal, business, or other (i.e. nonprofit, event) use. 47% of website managers were responsible for building their website; 24% were responsible for maintaining their website; and 28% were responsible for both building and maintaining their website.
All website managers were based in the United States.
48% have a personal website, such as a blog or portfolio. 34% are responsible for a business website, with the remaining 18% split between using their website for events or nonprofit and community work.
DIY web builders (38%) were the most popular website option among website managers. Additionally, 35% use advanced content management systems such as WordPress; 20% used a custom website; and 8% did not know what type of website they used.